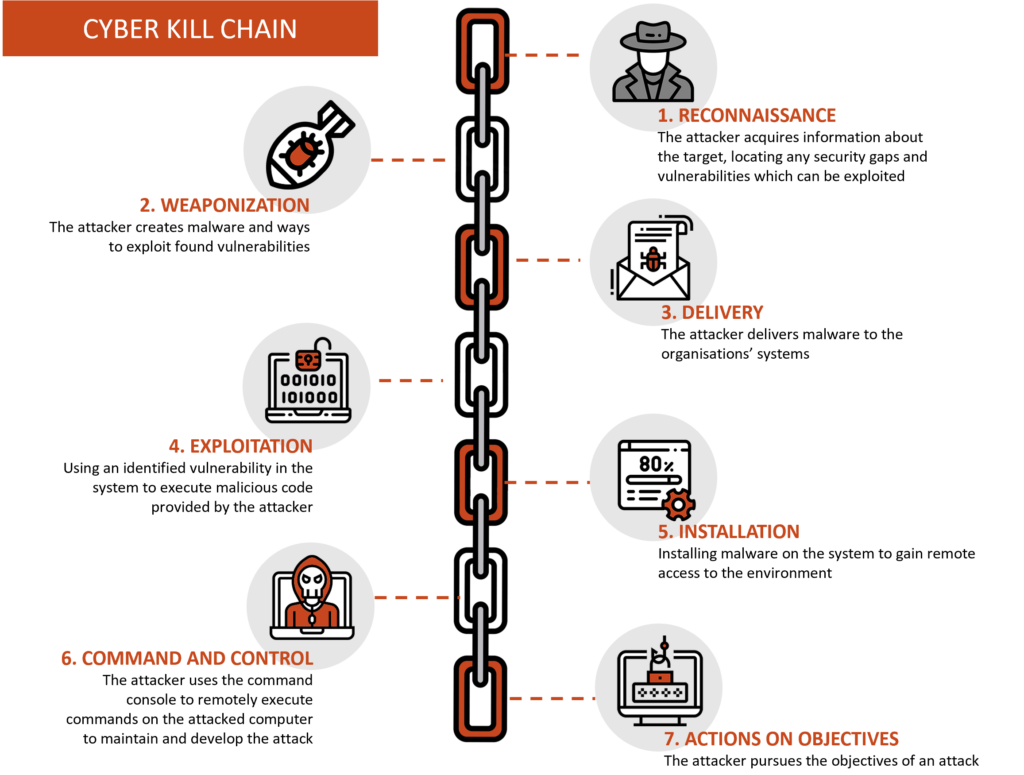
Zero-Day Exploits: What They Are and Why You Should Care
In cybersecurity, zero-day exploits are one of the most dangerous threats. If you work in IT or are starting to explore this world, it’s important to know what they are and how they can affect you.
What Is a Zero-Day Exploit?
A zero-day exploit is a security weakness in software or a system that even the developers don’t know about.
The term “zero-day” means there’s zero time to fix it before attackers can use it. In simple words, hackers discover and take advantage of this flaw before anyone can fix it.
A Market for Zero-Day Vulnerabilities
You might not expect it, but there’s a market for selling zero-day vulnerabilities.
On the legal side, companies like Google, Microsoft, and Facebook offer bug bounty programs. These programs reward people who find and report security issues.
For example, Google’s Vulnerability Reward Program pays anyone who reports a security bug in their services, like Chrome or Android. This helps Google improve security and gives ethical hackers recognition and rewards.
On the dark web instead, hackers sell these exploits to cybercriminals or groups for money.
Famous Zero-Day Exploits
Here are some real-world examples:
- Stuxnet (2010): A malware that attacked industrial systems, causing serious damage (USA + Israel vs Iran Nuclear program).
- Heartbleed (2014): A security flaw that exposed millions of sensitive data records (using a breach in the SSL protocol).
- Pegasus (2021): Spyware used to track journalists and activists through their phones (it’s a mix of different exploit for mobile OSs, probably still used …) .
Why Are They So Dangerous?
- They can’t be stopped immediately: There’s no update available until the flaw is found and fixed.
- Huge impact: They can affect entire companies and millions of users.
How to (try to) Protect Yourself
Here are some tips to reduce the risk and the damage:
- Keep everything updated: Software updates often include important security fixes.
- Use modern security tools: Firewalls, antivirus software, and intrusion detection systems help a lot.
- Backup your data regularly: If something goes wrong, you won’t lose everything.
- Stay informed: Learn about new threats and teach your team to recognize suspicious behavior.