The CIA Triad: Core Principles of Cybersecurity
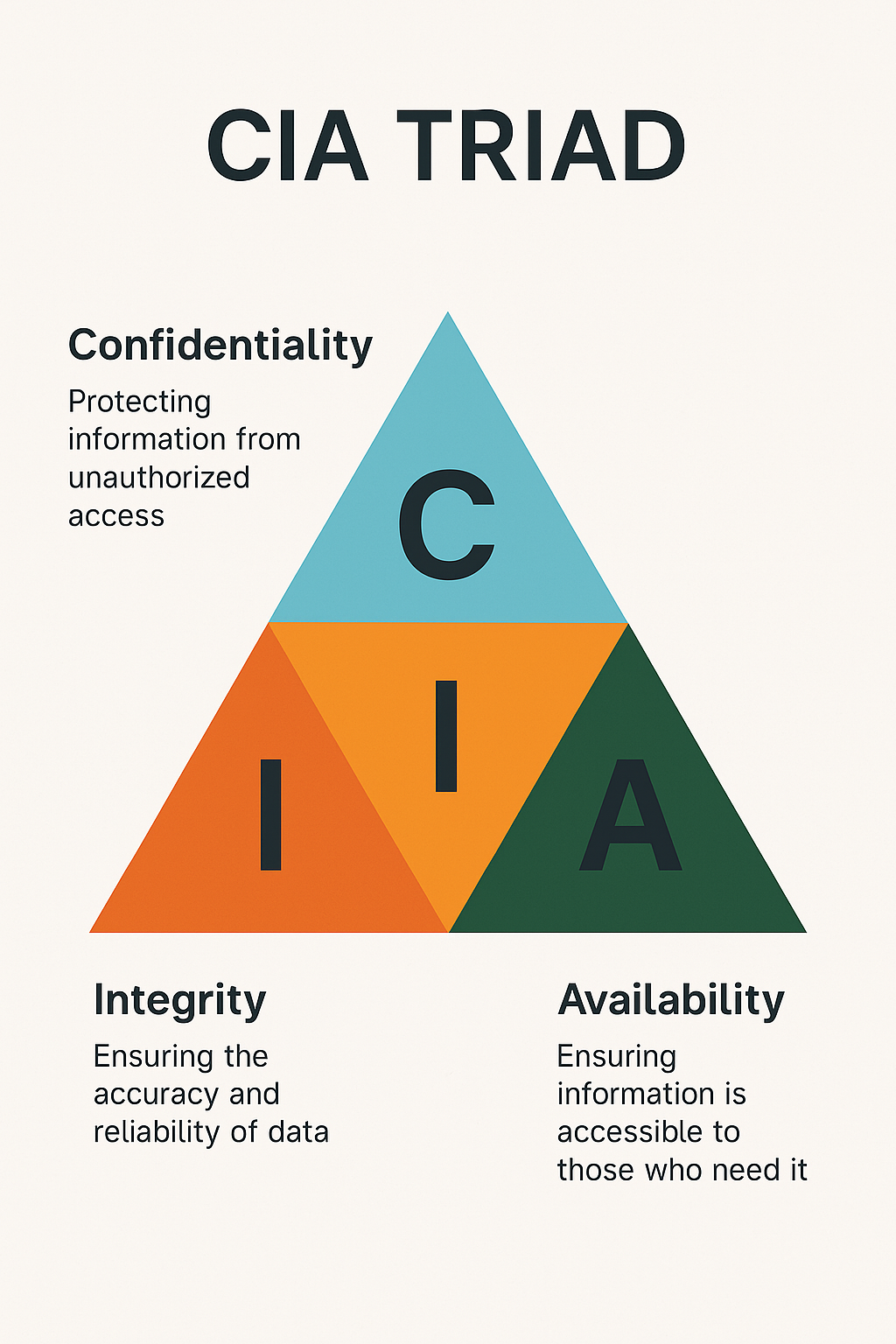
The CIA Triad
Three pillars define information security:
Confidentiality
- “Keep it secret.”
- Ensures data is only accessible to authorized parties.
- Tools: Encryption, access controls, RBAC.
Integrity
- “Keep it accurate.”
- Prevents unauthorized tampering or corruption.
- Tools: Checksums, digital signatures, versioning.
Availability
- “Keep it accessible.”
- Guarantees systems/data are available when needed.
- Tools: Backups, redundancy, DDoS protection.
Why It Matters
Every cyberattack targets at least one leg of the triad:
- Ransomware → Attacks availability.
- Data breaches → Violate confidentiality.
- Tampering → Compromises integrity.
🧠 Visual Summary